
Security on Android is always a debatable topic for any tech-enthusiast. Being an open source Operating System, Android source code is freely available to everyone which can be used to strengthen the OS further. However, security on Android is always a questionable topic as more and more bugs are being discovered which are exposing millions of Android devices to attacks. Last month, security company Zimperium announced a bug inside Android OS which grabbed a lot of eyeballs around the world. The “Stagefright” bug could potentially expose over a billion Android devices and the worst part is that the user won’t even know it.
You heard it right, a billion Android devices are at risk with this newly discovered vulnerability and that made us curious to know about it. So, what’s so-called “Stagefright”? And do we need to worry about it? Here’s what we know about this menacing bug and we’ll soon learn if we really need to take this serious.
So, What is Stagefright?
Stagefright is a remotely exploitable bug that affects almost every Android device running Android version 2.2 Froyo or above. The hard truth about this bug is that it lives fairly deep inside the Android core operating system itself which made things much worse. This bug allows the attacked to perform a remote code execution and privileged escalation just by sending a simple video via MMS. The libStageFright mechanism which helps Android OS to process video files will then execute the code unknowingly. This will provide an easy backdoor to the attacker to remotely exploit your device.
When the attacker video was processed on your device, the attack theoretically could happen without the knowledge of the user. Moreover, the hacker would have access to all the data on the device which can be used for malicious purposes. It’s also been mentioned that the attacker can potentially access the microphone, camera and Bluetooth on the device.
A Quick Patch
As soon as the word is out, Google has quickly acted to fix the Stagefright bug. In a short period, Google pushed updates containing the security patch to many of the Nexus devices and the OEM partners. Most of the popular OEMs like Samsung, HTC, and Motorola also responded quickly to roll out security patches to the popular devices. Google says that the security patch will mitigate the exploit but the folks at Exodus Intelligence says otherwise.
In a blog post, Exodus Intelligence warned “There has been an inordinate amount of attention drawn to the bug — we believe we are likely not the only ones to have noticed it is flawed. Others may have malicious intentions.” Google responds that more than 90% of the Android device are safe from this exploit, thanks to the ASLR (Address Space Layout Randomization) technique which will automatically confront such exploits.
How to detect Stagefright Vulnerability
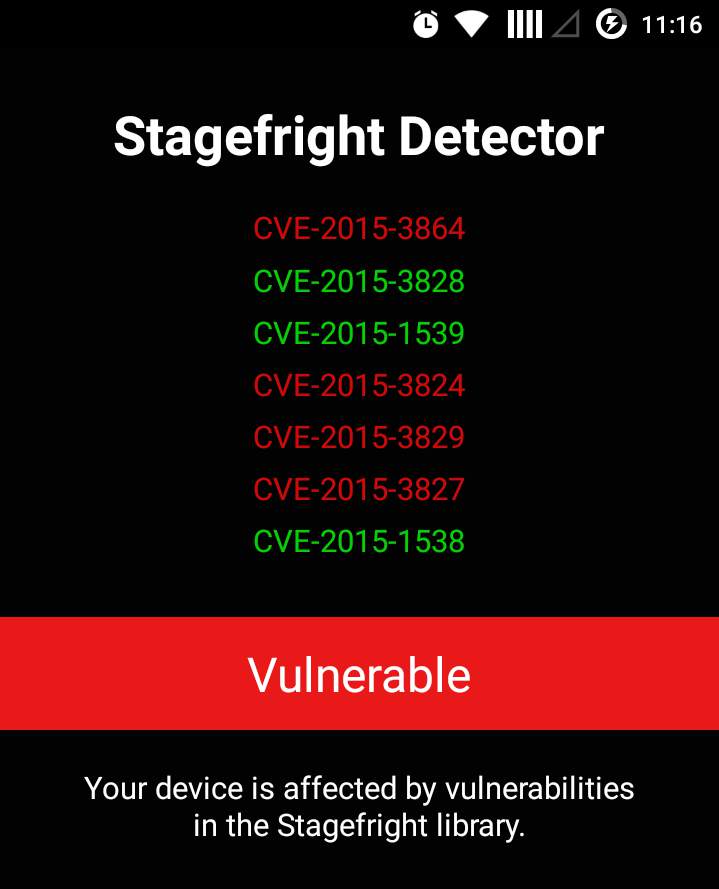
The folks at Zimperium have made an app that will detect whether your device is vulnerable to the Stagefright hack. The app is very simple to use, all you need to do is to click a button to test the vulnerability. The app will check for common vulnerabilities and exposures (CVEs) and let you know if your device is vulnerable. However, the app can’t fix the vulnerability but you can submit the anonymous stats to Zimperium for investigation which will help fighting this massive vulnerability in Android.
So, if you’re curious to see if your device is secure or not, download the Stagefright detector app from below link and check for vulnerability.
[googleplay url=”https://play.google.com/store/apps/details?id=com.zimperium.stagefrightdetector”]How to Protect your Device
Unfortunately, there is no imminent fix to the Stagefright bug since Hangouts and messenger apps auto-download videos by default. However, you can disable auto-download videos on your device, thus stopping the malicious code from executing in the first place. Firstly, you need to identify the default SMS/MMS app on your device and disable the “Auto-retrieve MMS” option. However, it’s better to disable the MMS option in all the messaging apps until we find a better workaround.
So, here’s how to turn off “Auto retrieve MMS” option in Hangouts
- Open the Hangouts app, and tap the hamburger icon (three horizontal lines on the top left) which is next to your name on the main screen.
- You’ll see a sliding menu, tap on Settings and then select SMS.
- Scroll down to Auto retrieve MMS option and un-check it if it’s already enabled.
Note: If the option is grayed out, then Hangouts is not your default SMS app. So, turn it off in the default messaging app that you use for all your messages.
The only good news is no hacker is currently using this exploit to attack Android devices as per the security analysts (or someone already using it?). However, it’s always better to keep the doors closed for unwanted guests, right? As Linus Torvalds quoted “Given enough eyeballs, all bugs are shallow” which is absolutely true in my opinion. Considering all OEMs are already working on the issue, we expect the bug to be resolved soon enough.



Join The Discussion: